Covert Comm Mobile App
Below you will find more details on how to sign up, login, hide & reveal files and lock and validate the integrity of your files. Please feel free to email us if you have any questions that were not covered in this guide
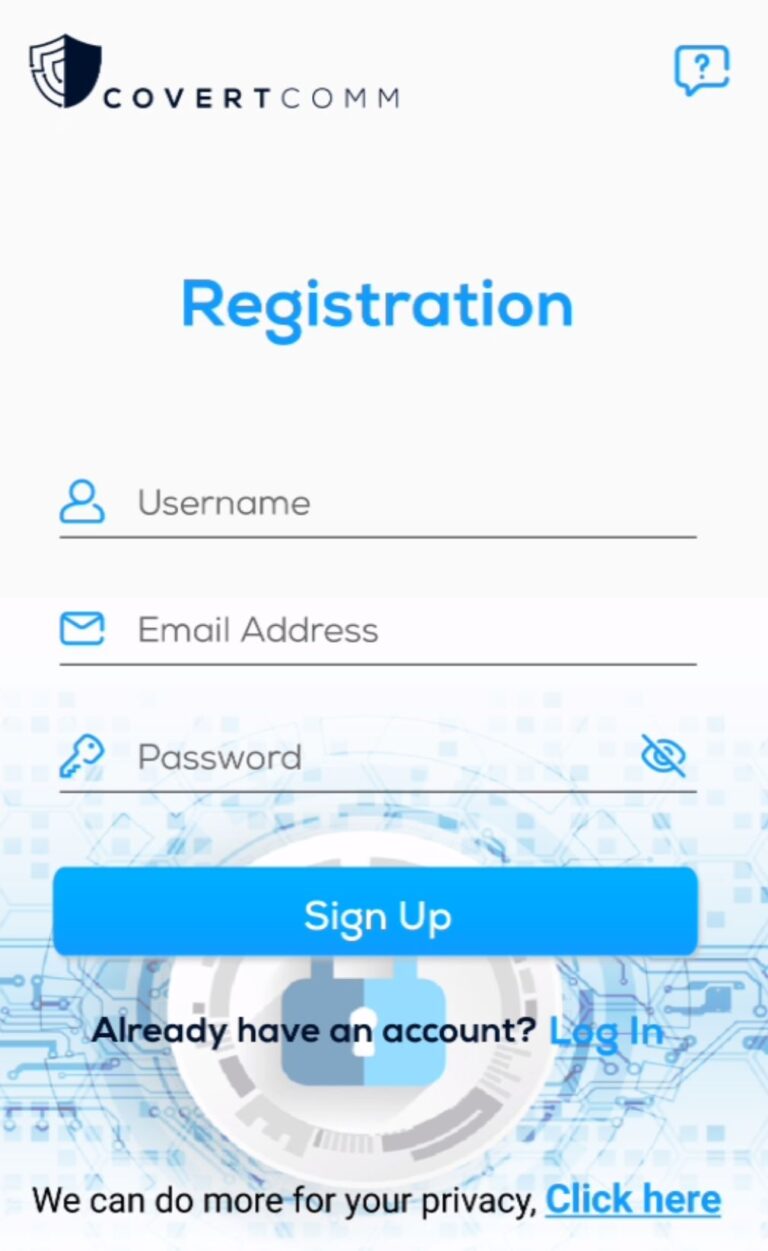
Sign Up
Please use the following steps to sign up to your app
1. From the main page on you app, Click Sign Up.
2. Enter your username, password & email address. Password must be at least 8 characters in length and must contain at least one Upper case letter, one lower case letter, one number and one special character.
3. Once submitted, you will see a message confirming “Success” and will receive an email address with the confirmation code.
4. The application will automatically take you to the next page, enter your 6 digits confirmation code.
5. Congratulation! you have successfully created an account and can start with securing your privacy.
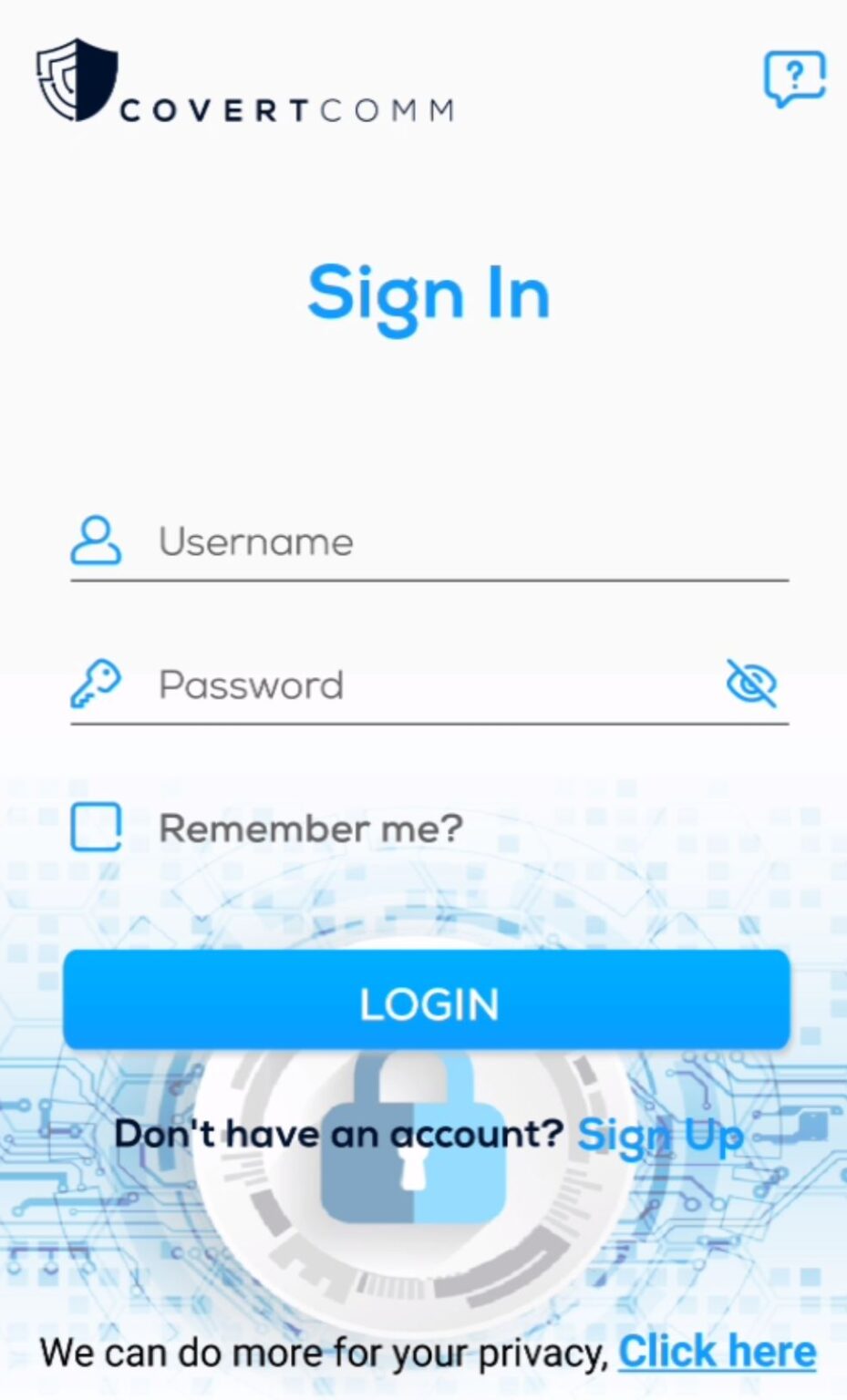
Login
To login to covert comm app. After launching the application just enter your username and password previously created.
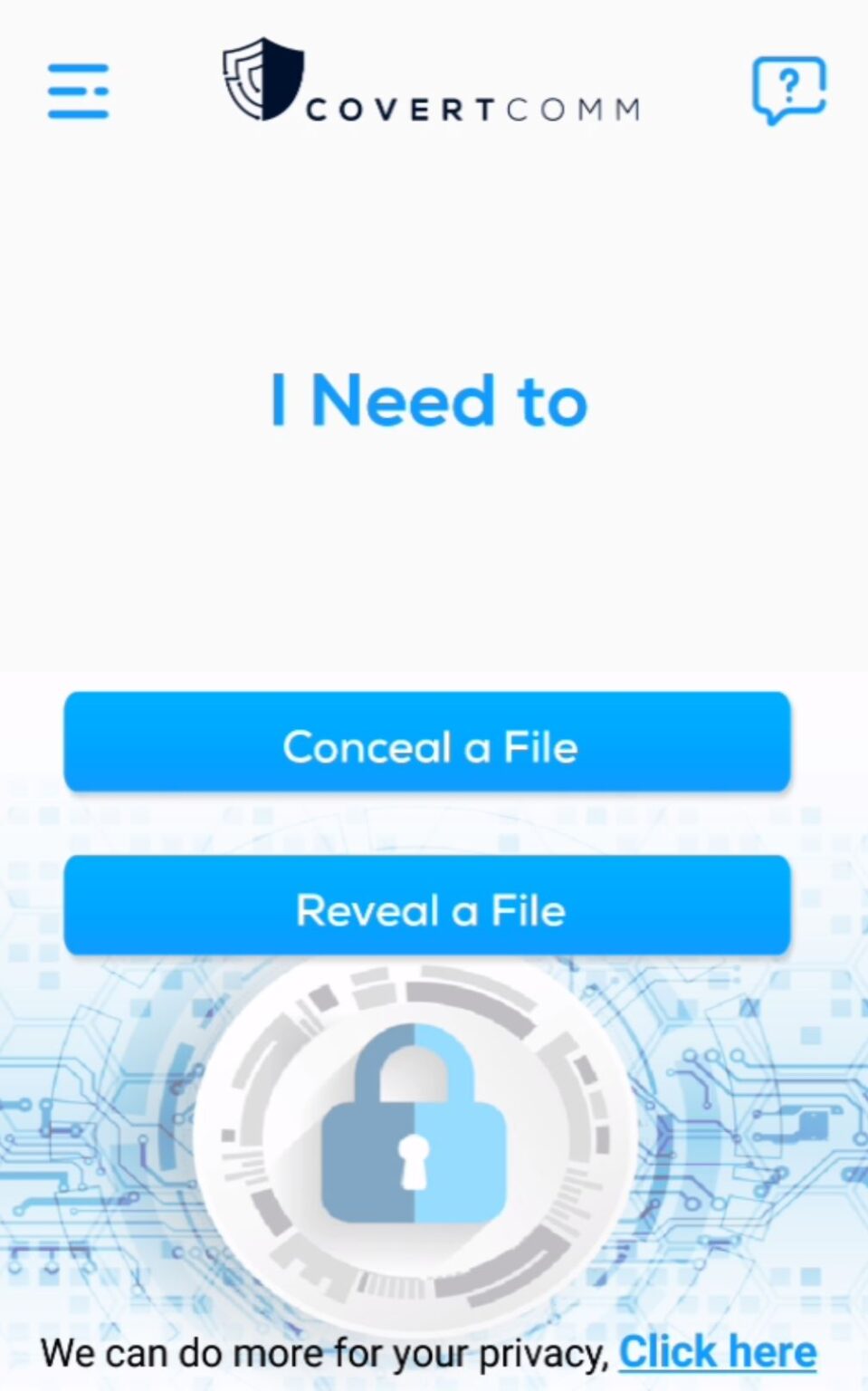
Covert Comm App offer two different pages
1- Conceal a File:
This page contains two forms “Conceal a File” and “Enable Tamper Detection”
The Conceal a File form allows you to hide any file or text message inside another file. We don’t only encrypt your data but we also hide it inside a file of your choice.
The Enable tamper detection allows you to apply an invisible stamp to your files which enables you later on to validate whether they were tampered with or can be trusted.
2- Reveal a File
The page contains two forms “Reveal a file” and “Validate a file”.
The Reveal a File form helps with extracting the sensitive data you previously concealed inside a file from the conceal a file form.
The Validate a File form allows you to validate whether a file (locked from tamper detection form) can be trusted or it was tampered with.
Conceal a File
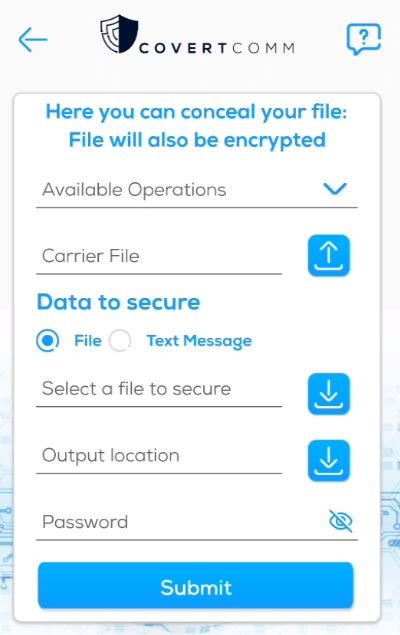
To Conceal a File Inside Another File
1. Available Operations: This shows the available file types which covert comm can hide files inside
2. Carrier File: Choose the file which you want to hide data inside. Covert comm will automatically set the operation type based on the file you choose.
3. Data to Secure: You can choose a file that you want to secure or enter a text message instead.
4. Output Location: this will be the location that covert comm saves the file to. Covert comm will take the payload message/file, hide inside the carrier file and save it in the same location as the file you choose here.
5. Password: this is a password you enter for securing that specific file. This can be different from your account password. You will need it later to extract the file
6. Finally, hit the submit button. Covert comm will show a message indicating success and the location the file was saved to.
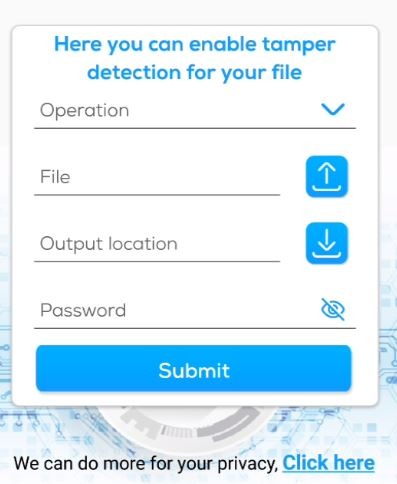
To Lock a File for Tamper Detection
1. Available Operations: This shows the available file types which covert comm can inject invisible detection technology
2. File: Choose the file which you want to enable tamper detection on
3. Output Location: choose any file, the new locked file will be saved in the same folder
4. Password: a password of your choice, the password will be used to inject the tamper detection. You will need it later to validate your file
5. Finally, hit submit and the new signed file will be saved to the selected location
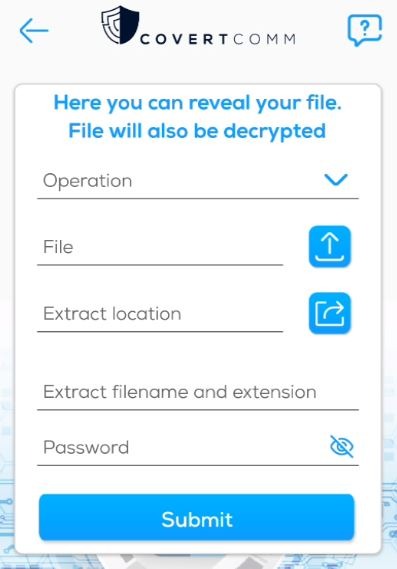
Extract / Reveal a File
To Extract or Reveal a File Inside Another File
1. Available Operations: This shows the available file types which covert comm can extract file files from
2. File: Choose a file that was saved from previous steps in the conceal a file form
3. Extract Location: Choose a file and covert comm will use the same folder to save the extracted file
4. Extract Filename and Extension: enter the desired file name and extension. For example if you previously concealed a bmp inside a pdf you can name the file “output.bmp”.
note: in case what you are extracting is a message, please make the extension as txt (i.e output.txt)
5. Password: the password you used to conceal the file previously
6. Finally, hit the submit button. Covert comm will show a message indicating success and the location the file was saved to.
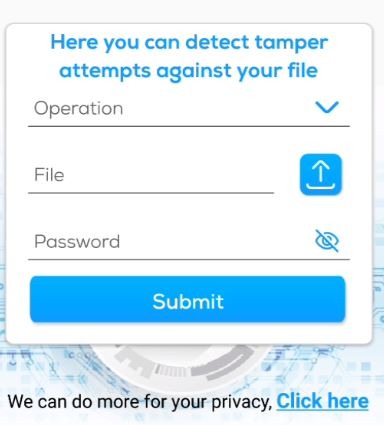
Tamper Detection
1. Available Operations: This shows the available file types which covert comm can inject invisible detection technology
2. File: Choose the file which you want to validate
4. Password: enter the password you used earlier to enable tamper detection on this file
5. Finally, hit submit and you will receive a message on whether this file was tampered with or can be trusted.